Set up the authentication provider in TotalAgility Designer
In TotalAgility Designer, set up the federated security authentication provider that supports the SAML standard.
-
In
TotalAgility Designer,
navigate to
.
The Federated security dialog box is displayed.
- Click the Add icon to add a new provider.
- Use the following tabs to configure the settings for the authentication provider:
-
Click
Save.
The authentication provider is added to TotalAgility and the Federated security dialog box is displayed.
Once the authentication provider is added to TotalAgility, you must enable federated security.
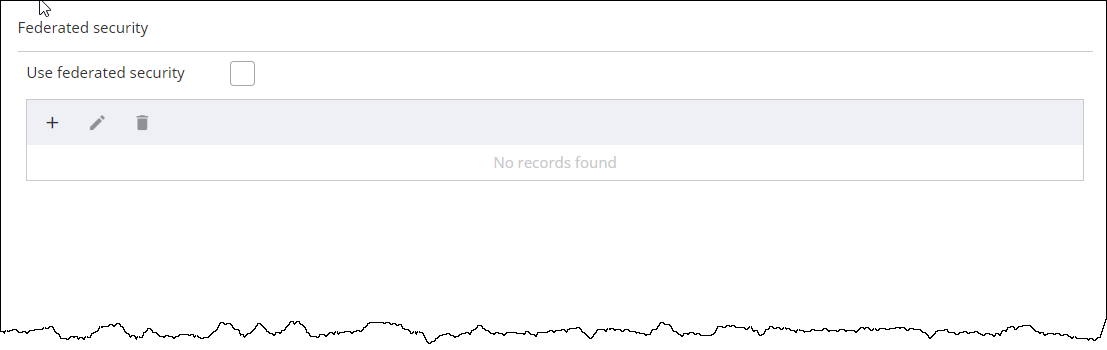
General
Use the General tab to configure the general settings.
| Setting | Description |
|---|---|
|
Name |
Use any text to enter the authentication provider’s name. |
|
Endpoint type |
Select SAML as the endpoint type. The endpoint type is selected based on the federated authentication types supported by the provider. |
|
Endpoint URL |
Enter the authentication provider's endpoint URL. |
|
Binding type |
Specify the authentication binding type as HTTP Redirect for this provider. The authentication binding type depends on the binding type supported by the provider. |
|
Authentication context |
Select how a user is authenticated by an Identity Provider. |
|
Relying party |
Leave it blank. |
|
Issuer |
Enter the authentication provider's issuer URL. This URL is defined by the provider. |
|
Sign out URL |
Leave it blank. |
|
Logout |
TotalAgility |
|
Active |
Selected |
|
Relay state only |
Leave it clear. This setting is only available for the SAML endpoint type. |
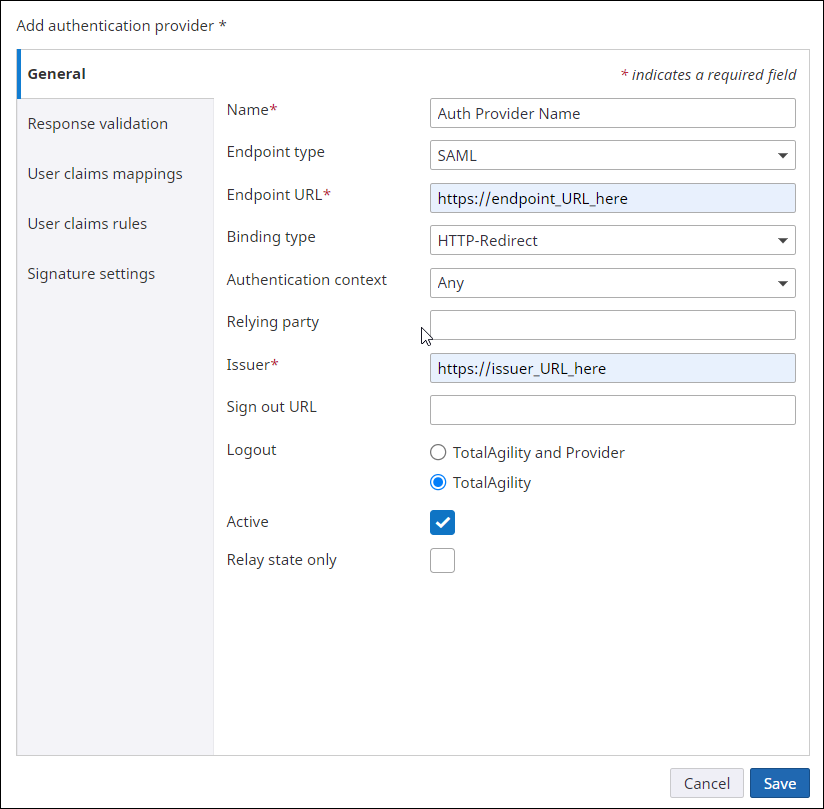
Response validation
Use the Response validation tab to configure the response validation for the authentication provider.
TotalAgility must validate the signed authentication response from the provider to ensure it is trusted. Therefore, you must add the certificate thumbprint obtained from the authentication provider. A sample certificate (Cert.txt) is available for this purpose when you expand the "Getting Started" section of the TotalAgility Documentation page.
Make sure that the certificate matches the one provided by the authentication provider.
You can specify up to three certificate thumbprints to validate the response from the authentication provider. Multiple certificates help providers who use rolling certificates that are updated intermittently.
-
Download Cert.txt to your computer.
-
Open the Cert.txt in Notepad.
-
Copy the entire content, and paste it in the Certificate1 box.
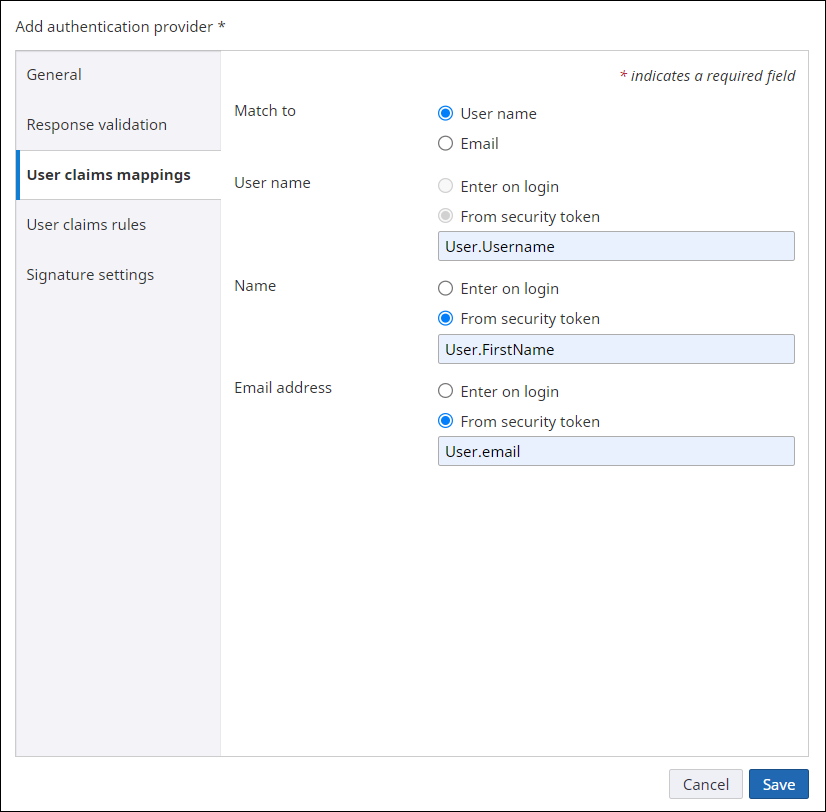
User claims mappings
Use the User claims mappings tab to specify mappings from the security token claims returned by the authentication provider to the user settings in TotalAgility.
| Setting | Description |
|---|---|
|
Match to |
Indicates if the user will be matched in TotalAgility based on the username, or email address. This is used to determine if the user already exists in TotalAgility after successful logon with the authentication provider.
|
|
User name |
Indicates if the username is from a security token claim or entered manually on the first logon. This is used when automatically adding the user to TotalAgility on initial logon. If "Match to" is set to User name, you must map the username to a Claim Type (it cannot be entered on logon). The value for the mapped claim type must be unique for that user in the authentication provider.
|
|
Name |
Indicates if the name is from a security token claim or entered manually on the first logon. This is used when automatically adding the user to TotalAgility on initial logon.
|
|
Email address |
Indicates if the email address is from a security token claim or entered manually on the first logon. This is used when automatically adding the user to TotalAgility on initial logon. If "Match to" is set to Email Address, you must map the email address to a claim type (it cannot be entered on logon).
|
User claims rules
Use the User claims rules tab to configure user claim rules.
Select the category, working category, and working group for the corresponding user created in TotalAgility after successful authentication with the authentication provider on initial logon.
In this case, each user is assigned to the default category and
default working category and added to the Users group.

Configure user claims custom rules
You can define a set of custom rules to further indicate the worker group in TotalAgility a user is added to after successful authentication with the authentication provider on initial logon.
You can optionally use these rules to set the category, working category, and working group to values other than the default user claim settings.
You can specify all the working groups the user is added to in TotalAgility based on multiple claim values.
TotalAgility also supports multi-value claims where the same claim type can be specified multiple times checking for a different value each time.
To add custom claims rules, on the User claims rules tab, select Use custom user rules.
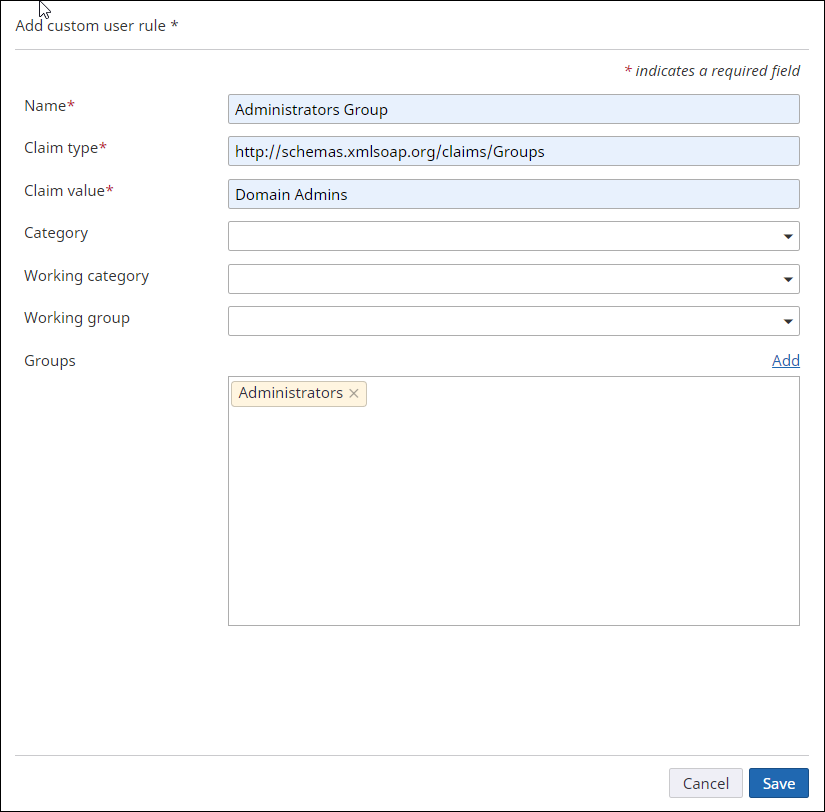
Add the first rule
-
Click
under
Custom user rules.
The Add custom user rule dialog box is displayed.
-
If there is a claim of type
http://schemas.xmlsoap.org/claims/Groups for
the user with a claim value of Domain Admins, then add this user to the
Administrators working group in
TotalAgility
(if the user does not already exist there) as shown below.
- Click Save.
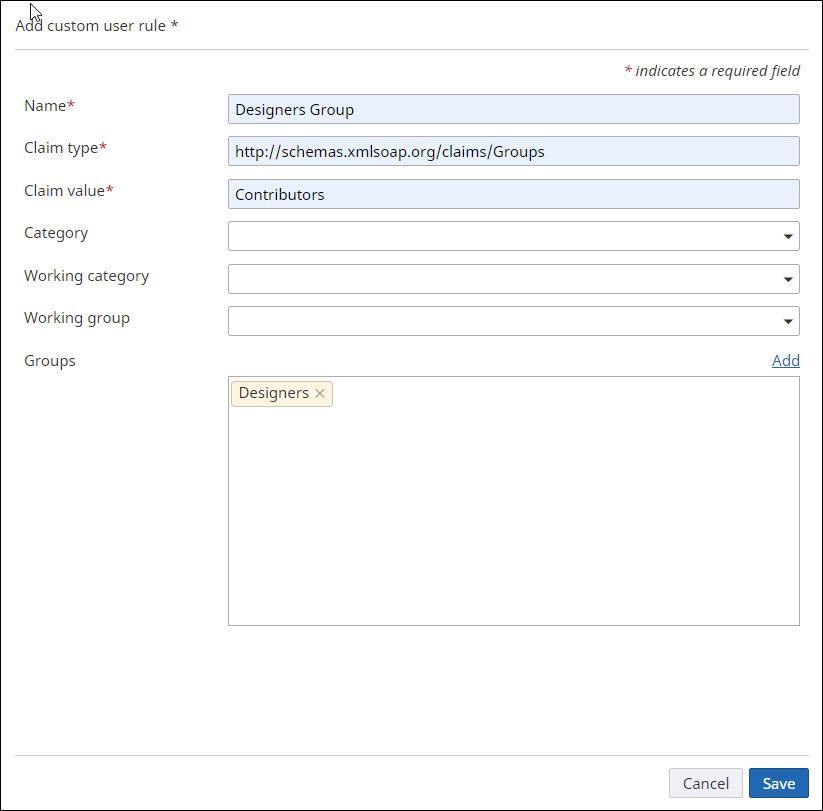
Add the second rule
-
Click
under
Custom user rules.
The Add custom user rule dialog box is displayed.
-
If there is a claim of type
http://schemas.xmlsoap.org/claims/Groups for
the user with a claim value of Contributors, then add this user to the
Designers working group in
TotalAgility
(if the user does not already exist there) as shown below.
- Click Save.
Add the third rule
-
Click
under
Custom user rules.
The Add custom user rule dialog box is displayed.
-
If there is a claim of type
http://schemas.xmlsoap.org/claims/Groups for
the user with a claim value of Marketing Team, then add this user to the
Marketing working group in
TotalAgility,
if the user does not already exist there.

- Click Save.
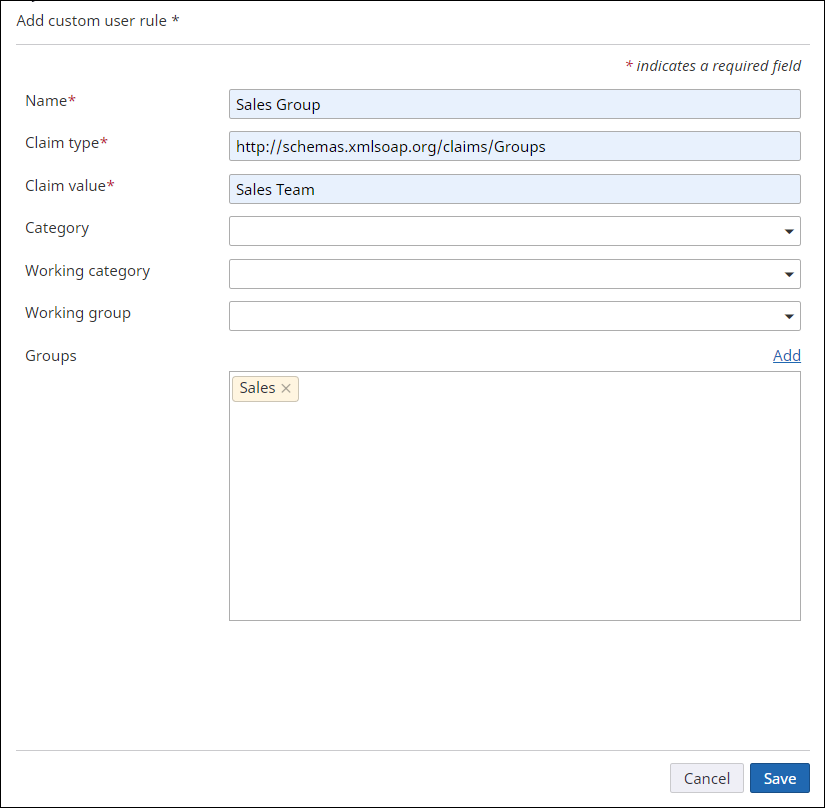
Add the fourth rule
-
Click
under
Custom user rules.
The Add custom user rule dialog box is displayed.
-
If there is a claim of type
http://schemas.xmlsoap.org/claims/Groups for the user with a claim
value of Sales Team, then add this user to the Sales working group in
TotalAgility
(if the user does not already exist there) as shown below.
- Click Save.
Signature settings
Use the
Signature settings tab to
specify a certificate used to sign the authentication request made by
TotalAgility
to the authentication provider. This setting is dependent on the
security requirements of the authentication provider.
We will skip this setting for this use case, as we do need a certificate for signing the authentication request made by TotalAgility.