Add Identity
Add the identity of a user, such as name and mail ID, for reading the RPMSG messages.
Prerequisites
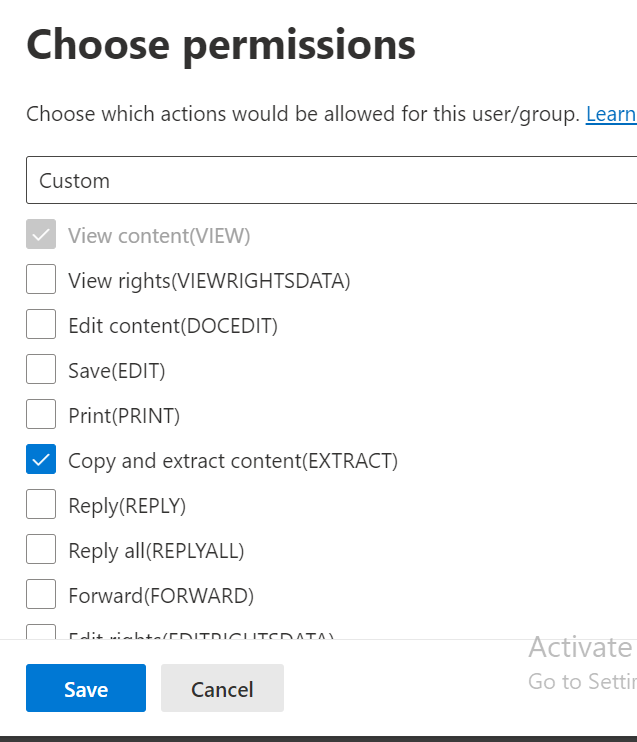
Following is the minimum set of Azure Rights Management Services (RMS) permissions required to be configured in the client applications.
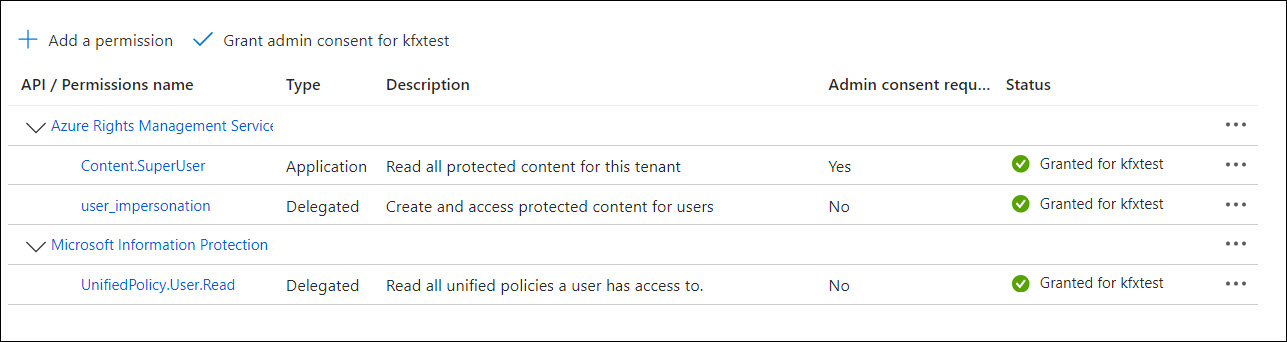
- Open the KC Plug-In window and click the Identities tab.
-
On the
Identity tasks menu, click
Add Identity.
The Identity pop-up window is displayed.
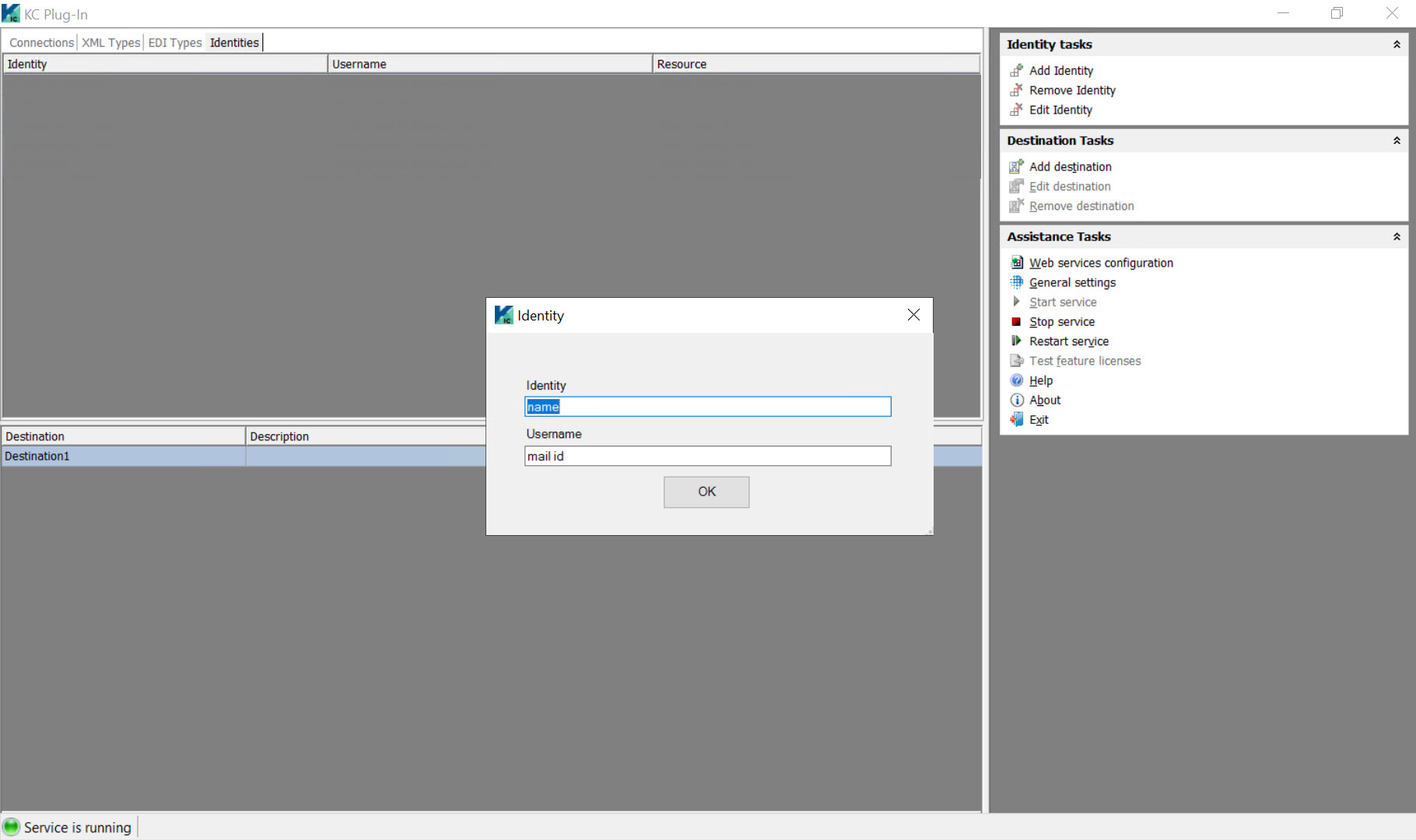
-
Do the following:
- In the Identity box, enter a unique name for the Rights Management Identity.
-
In the Username box, enter the mail ID of the user who is authorized to read an RPMSG message.
-
Click OK to close the Identity pop-up window.
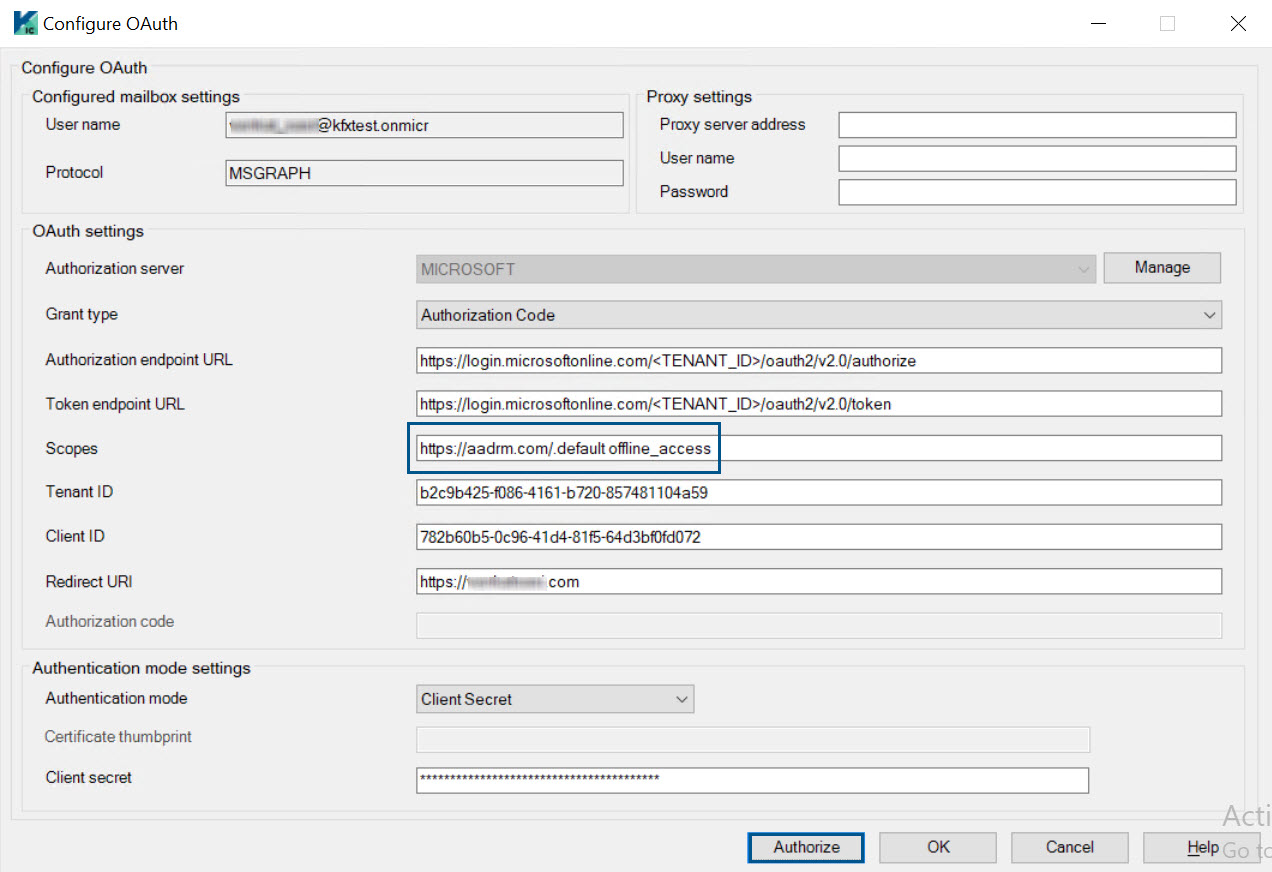
The Configure OAuth dialog box is displayed.
-
Configure OAuth settings to get the OAuth token for the rights management user. For more information, see
OAuth settings.
Make sure to enter the following value in the Scopes box to provide permission for accessing the Azure AD Rights Management (AADRM) resource:
-
For Authorization Code grant: https://aadrm.com/.default offline_access
-
For Client Credentials grant: https://aadrm.com/.default
-
-
Click
Authorize to get the OAuth tokens.
RPMSG message processing is currently supported for Client Credentials and Authorization Code grants only.
A confirmation message is displayed if authorization is successful.
-
Click
OK to close the message pop-up window and then click
OK to close the Configure OAuth dialog box.
An access token is added to the "OAuth2TokenCache.cache" file in the C:\ProgramData\Kofax\KIC-ED\KCPlugIn\config folder. The access token can be identified from the "Identity name" provided while adding the identity.
The newly added identity is listed in the Identities tab.
- If for some reason authorization fails, make sure to click the Cancel button in the Configure OAuth dialog box, so that a new row is not added to the Identities tab.
-
If authorization fails and the OK button is clicked, a new row is added highlighting the entry in red.
Configuring external identities for decrypting cross-tenant RPMSG messages
You can use the External Identities feature in Microsoft 365 admin center to acquire Azure RMS (Rights Management Services) tokens for decrypting the RPMSG messages from an external tenant.
For instance, if a customer ‘A’ receives RPMSG messages from his clients ‘B’ and ‘C’, then customer A requires a mail ID to be registered with clients B and C as an external identity. Also, customer A must be added to the data protection label permissions list created by clients B and C (in Microsoft compliance portal), respectively.
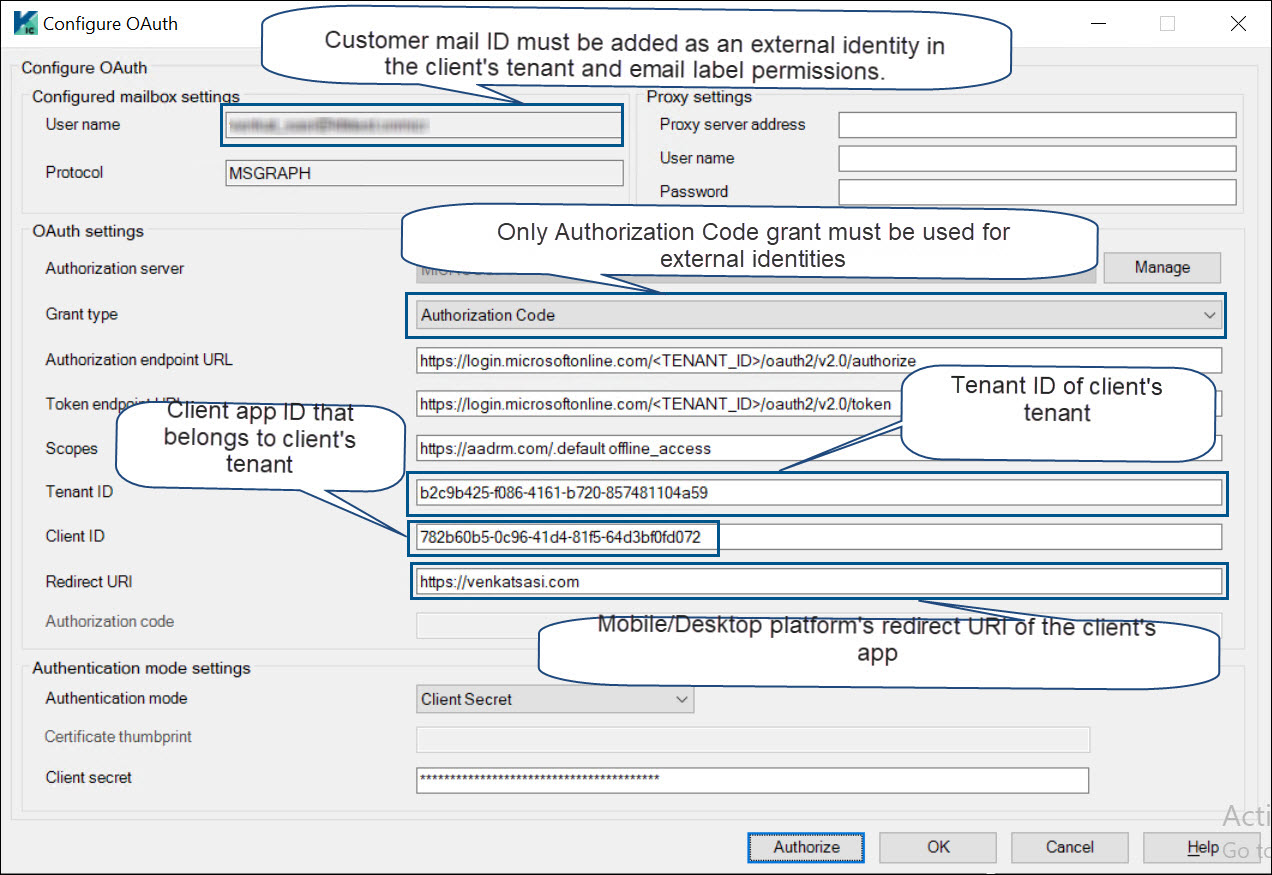
Clients B and C must share the details of their tenant ID, client ID, and redirect URI (from mobile and desktop application platforms in Azure portal) to customer A. Customer A can use these details to log in to the respective client’s tenant using customer A's mail ID and request RMS access tokens to decrypt RPMSG messages.
Use the following Microsoft link to configure B2B collaboration cross-tenant access.
Configure B2B collaboration cross-tenant access - Microsoft Entra External ID | Microsoft Learn
Ensure the following while fetching the RMS (Rights Management Services) token for an external user:
-
RMS token is fetched using a customer's mail ID registered with the respective client as an external user.
-
Only Authorization Code grant is used for fetching RMS tokens from the client.
-
The customer needs to be provided with Client Secret to use Client Credentials grant.
-
The client's tenant ID is entered in the Tenant ID box.
-
The client's application ID that has required permissions for RPMSG message decryption is entered in the Client ID box.
-
Redirect URI of mobile/desktop applications platform is entered in the Redirect URI box.
-
The Client Secret box is left empty.
Once the above steps are verified, click the Authorize button in the OAuth configuration window.
Provide the customer's credentials in the pop-up window for fetching the RMS token.
Example of OAuth configuration details for external user.
Configure destination for Rights Management Identity
A Rights Management Identity must be selected in the destination configuration in KC Plug-In for sending the corresponding access token to Message Connector for decrypting the RPMSG message.
-
In the
KC Plug-In window, select the destination configuration you want to modify
and click
Edit Destination.
The Destination configuration screen is displayed.
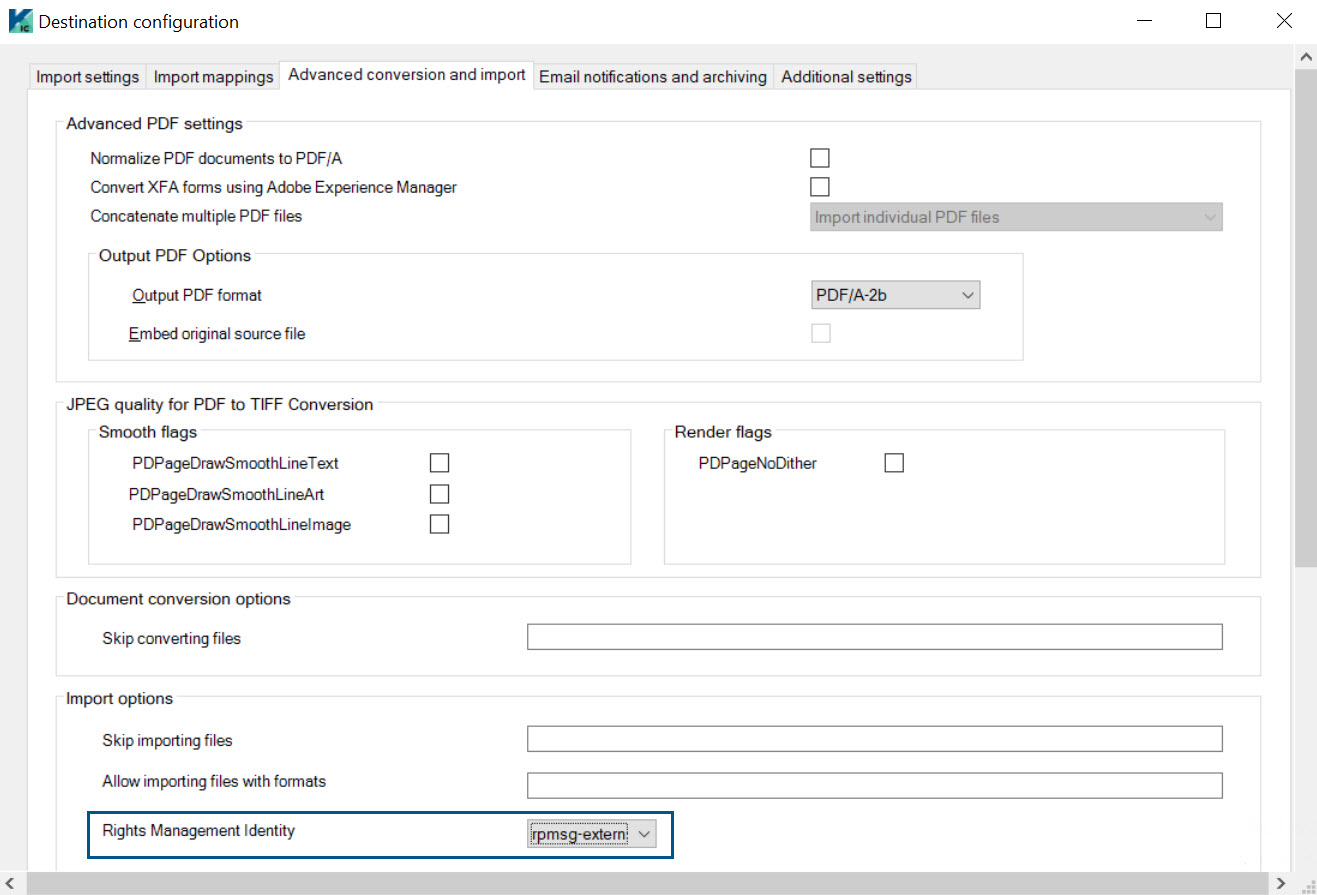
- Click the Advanced conversion and import tab.
- In the Import options section, select the relevant Rights Management Identity from the list.
- Click OK.
-
Restart the KC Plug-In service.
-
The identities which are displayed in red in the Identities tab are not displayed in the Rights Management Identity box.
-
While importing an RPMSG email, the rights management access token is passed to Message Connector. This token is used by the RpmsgDecryptor tool for decrypting the RPMSG message into a .msg file, which is later processed for conversion.
-