No connection to Active Directory server
You cannot sign in with your network username and password.
Resolution for user: Contact your administrator.
Resolution for administrator:
-
Select Active Directory authentication settings.
-
A computer with Printix Client must be online on Network1, otherwise, the on-premise Active Directory server cannot be contacted for authentication.
-
If it does not work with secure LDAPS, it could be a result of certificate errors.
Secure LDAPS certificate errors
Verify certificates and the certificate chain
Follow the instructions below to verify the certificates on the Active Directory server (Domain Controller):
-
Press
Windows+R.
The Run dialog box appears.
- Type: mmc, and select OK to open the Microsoft Management Console.
- On the File menu, select Add/Remove Snap-in.
- In the Add or Remove Snap-ins dialog box, select Certificates and select Add.
- In the Certificates snap-in dialog box, select Computer account and select Next.
- In the Select computer dialog box, select Another computer, and select Browse.
- In Enter the object name to select, type the hostname of the Domain Controller (such as DC01). Select Check Names.
- Select OK.
- Select Finish.
- Select OK.
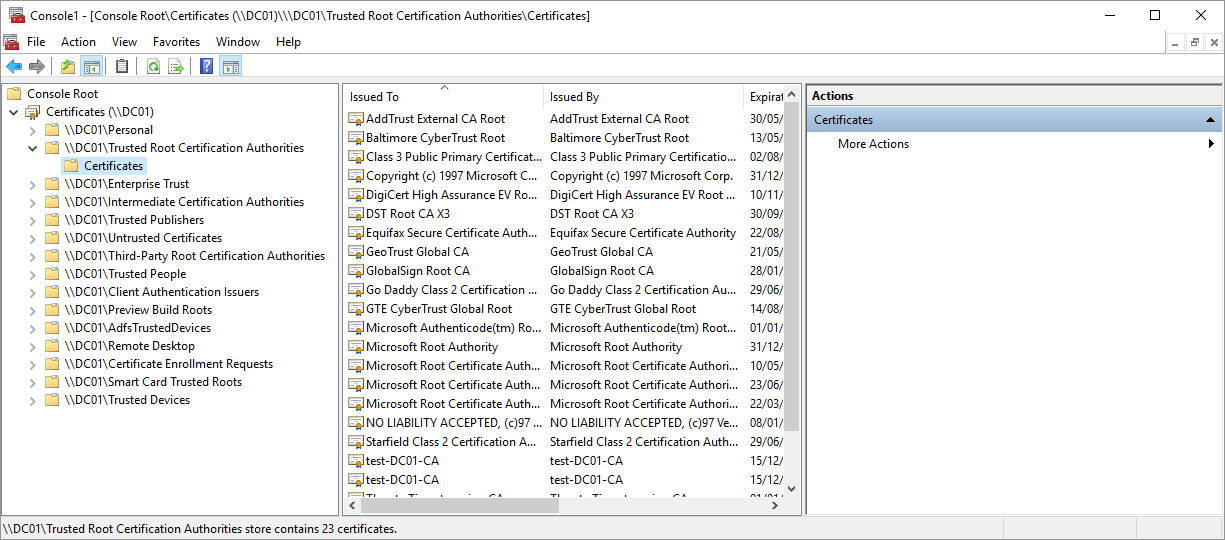
- The Microsoft Management Console now includes the Certificates snap-in for the Domain Controller (DC01).
- Expand Trusted Root Certification Authorities to see a list of the certificates.
- Open each certificate. Select the Certification Path tab, and select the Certificate status.
-
Verify that the certificates in the certificate path are stored accordingly in:
-
Trusted Root Certification Authorities
-
Intermediate Certification Authorities
-
Import certificate to the local machine certificate store
As the Printix Service (PrintixService.exe) runs under the local system account, the certificate used for Secure LDAPS connection, must be in the Local machine certificate store on the users' computers. If any of the certificates in the certification path are only stored in the Current user certification store, then Active Directory authentication will not work.
-
Local machine certificate store
This type of certificate store is local to the computer and is global to all users on the computer. This certificate store is located in the registry under the HKEY_LOCAL_MACHINE root.
-
Current user certificate store
This type of certificate store is local to a user account on the computer. This certificate store is located in the registry under the HKEY_CURRENT_USER root.
To resolve this, the certificate file must be installed on each computer:
The steps below are the same if you use certmgr.msc instead of mmc. To update multiple computers, consider using command line utility, Microsoft Certificate Manager Tool (certmgr.exe).
-
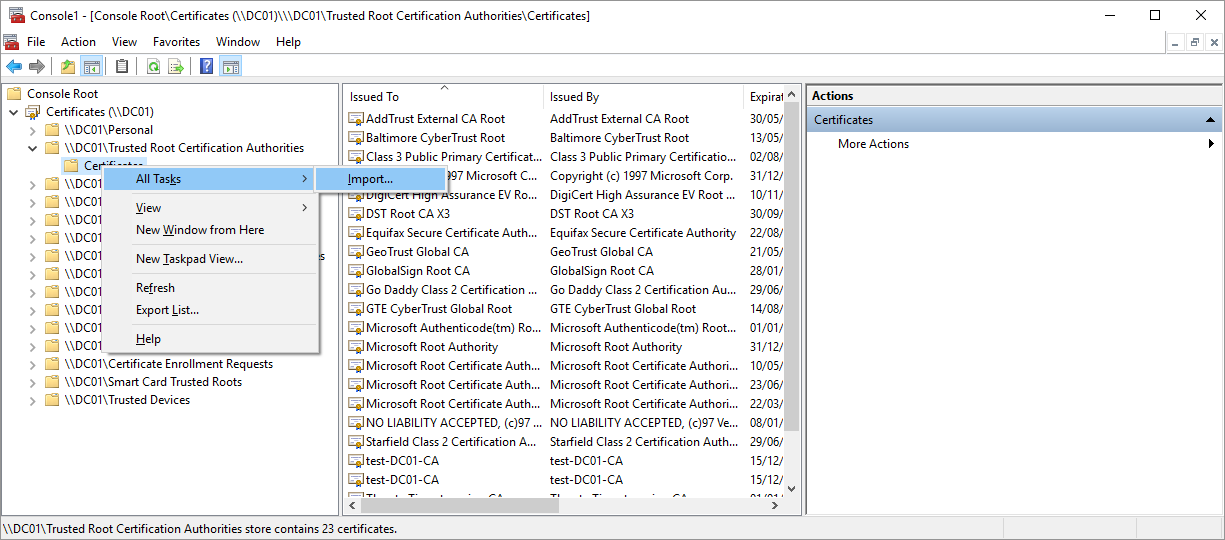
Right-click
Trusted Root Certification Authorities, select
All Tasks and select
Import.
The Certificate Import Wizard appears.
- Select Next.
- Browse to and select the folder with the certificate file.
- Select X.509 Certificate (.cer or .crt) and select All files.
- Select the certificate file and select Open.
- Select Next.
- Select Browse.
- In the Select Certificate Store, select Show physical stores.
- Scroll to the top and select Trusted Root Certification Authorities.
- Select Local Computer, select OK.
- Select Next.
- Select Finish.
Microsoft certificate error codes
-
CertEXPIRED = 0×800B0101
-
CertVALIDITYPERIODNESTING = 0×800B0102
-
CertROLE = 0×800B0103
-
CertPATHLENCONST = 0×800B0104
-
CertCRITICAL = 0×800B0105
-
CertPURPOSE = 0×800B0106
-
CertISSUERCHAINING = 0×800B0107
-
CertMALFORMED = 0×800B0108
-
CertUNTRUSTEDROOT = 0×800B0109
-
CertCHAINING = 0×800B010A
The certificate chain up to the Root Certification Authority (CA) is not found or invalid.
-
CertREVOKED = 0×800B010C
-
CertUNTRUSTEDTESTROOT = 0×800B010D
-
CertREVOCATION_FAILURE = 0×800B010E
-
CertCN_NO_MATCH = 0×800B010F
The certificate does not contain the name of the host we are trying to connect to.
-
CertWRONG_USAGE = 0×800B0110
-
CertUNTRUSTEDCA = 0×800B0112